QAC EmTech
QAC Emerging Technologies Quality Assurance
This monthly newsletter will focus on QAC’s activities regarding R&D,Connected Vehicles, Cognitive Autonomous Systems, Artificial Intelligence,Internet of Things, and Blockchain Quality Assurance Services.
FOCUSED ON THE FUTURE
Leading the way
Welcome to the tenth edition of the EmTech newsletter. In this edition, we’llbe sharing more about state-of-the-art of automotive cybersecurity. In previous newsletters, we talked about sensor attacks that frequently occur with automotive vehicles. This newsletter will focus on exploring software attacks as well as attacks conducted through wireless communication as a part of network attacks.
Welcome to our 10th edition of our EmTech Quality Assurance Newsletter
Keeping you informed
Our emerging technologies quality assurance workstreams
R&D and Grant Projects
Research and development of new technologies that position QAC to become a world leader in quality assurance services.
Connected Vehicles
Testing and Quality Assurance services exclusively developed to provide integration testing services for highly connected vehicles.
Cognitive Autonomous Systems
Fully automation of testing and quality Assurance services exclusively developed for Cognitive Autonomous Systems
Cybersecurity, IoT, AI, and Blockchain
Focus on developing new technologies that utilizes AI to address QA challenges on Cybersecurity, IoT, and Blockchain domains
Automotive sensors
Automotive software incorporates various requirements such as safety, cybersecurity, usability, and performance.
When it comes to car, diesel engines, or electric cars, there are many sensors in the Electronic Control Unit (ECUs) such as Cameras, LiDAR, Radars, etc. As the connected vehicle auto industry market increases at a rapid pace, so do the opportunity for attacks on motor vehicles. Older vehicles relied on physical parts and were difficult to hack. However, today’s cars are computers on wheels and are equipped with more features and amenities than ever before. As a result, new vehicles are seen as a challenge, from a hacker’s perspective, and automotive manufacturers need to invest in preventative cyber protection to keep owners safe. The average car has millions of lines of code which gives attackers plenty of opportunities to test their skills. Sophisticated hackers could exploit automotive software and access any vehicle. Consequently, it will come as no surprise when the news reports an increase in the number of software attacks against infotainment systems, charging stations, and mobile apps, etc.
Software attacks
When software is attacked, the intent is to disable to software executed on each component such as the sensors, radar, etc. The following is a list of common automotive software-related attacks.
Infotainment
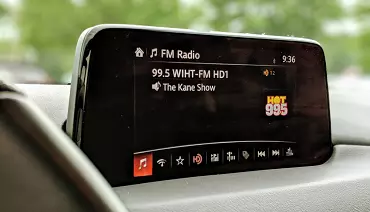
Infotainment is defined as a combination of vehicle information and entertainment systems. It is becoming more and more essential as we move toward smart vehicles. It provides an audio/video interface, such as a touch screen, and a voice command option to the occupant(s). Many modern vehicles are connected to the internet via infotainment systems, which allow for interconnectivity vulnerabilities. Infotainment systems can be classified as both input attacks and software-related attacks. Infotainments typically run operating systems using Android, Integrity real-time operating system (RTOS), Linux, QNX, and Windows Embedded Automotive. Additionally, infotainment systems are often accessible via a USB connection, Bluetooth, and in some instances Wi-Fi-enabled devices.
Given the attack vectors of a typical operating system, this allows connected vehicle operating systems to be susceptible to such operating system attacks. Common familiarity with these operating systems, allow hackers to transfer knowledge from computers to vehicles. In these devices, the attack surface is significantly reduced when compared to a traditional operating system. There are many realistic potential areas of attack such as ransomware, crypto mining, keylogging, and rootkits, etc.
Firmware
Firmware is a class of software designed to provides low-level control for a device’s specific hardware. Custom firmware is an unofficial new or modified version of firmware which usually is used to unlock hidden functionality or add new features to the system. Typically, hackers take advantage of such custom firmware to install or run their software. Having control over the firmware enables attackers to evade traditional security and have access to the highest levels of privilege on the device.
Firmware attacks include vulnerabilities in the firmware itself. Attacks may be a result of over the air updates used to squash bugs within the system itself and physical updates by connecting to an external device. When it comes to attacks, firmware updates for automotive control units are a potential weak spot. BIOS and newer UEFI systems are common points of firmware attacks. Firmware modification attacks are a primary area of concern. Firmware changes may affect the overall system itself. Such an attack is capable of providing false information, hiding malicious software (rootkits, modifying packets that are sent), and can be used as a staging platform for further malicious software such as dropping exploit kits.

Integrated & third-party applications
Software attacks do not necessarily affect the vehicle itself but rather provide additional access to unlocked areas accessed through the infotainment system itself. These exposed channels provide potential entry points to the hardware access layer (HAL). Once this point has been compromised, with malicious intent, the applications may provide access to areas of the vehicle. In turn, such an attack could affect multiple layers in the CIA triad (Confidentiality, integrity, and availability) and potentially be fatal to occupants.
Through attacks such as remote injection, rootkits, malware, ransomware, or other various areas, the security application itself provides access to the infotainment system and personal data a driver or passenger creates, uploads, or stores within these applications. This information could then be leveraged for additional attacks on the user or their vehicle in the future.
Wireless attacks
Wireless attacks related to the attacks through automotive wireless communication channels such as Bluetooth, Wi-Fi, MirrorLink, Remote Keyless Entry as listed below.
Bluetooth
Bluetooth has been used in some vehicles since 2010. Bluetooth is a networking capability used to connect a mobile device or third-party device to a vehicle’s infotainment system. There are various security auditing tools that exist which depend on the version of Bluetooth. Bluetooth 5.0 is the latest version of the Bluetooth wireless communication standard. However, it has encryption vulnerability as it is based on a 20-year-old standard.
Since Bluetooth is a widely used standard within vehicles, a close-range hack attempt can intercept data and images passed between both vehicle and mobile phone. Additionally, BlueBorne, Carwhisperer, Bloover II, blue diving and several other data leak vulnerabilities create quite a large attack surface for vehicular communications.
Wi-Fi
Another added functions to the vehicle are Wi-Fi connection which needs strong security measures to prevent any intrusions that could threaten drivers, passengers, and others. Similar to Bluetooth, Wi-Fi is a more stable and secure option when considering vehicle connectivity since it links to the internet and the capabilities of the car. However, it facilitates the potential for remote attacks. In cases where an Android phone connects to the vehicle, Wi-Fi information may be stolen if the device itself is compromised. Eavesdropping or hacking these channels has been proven possible utilizing systems such as man in the middle attack and Wi-Fi spoofing. In these cases, vulnerabilities that leverage and attack WPA encrypted networks further extend the attack surface of vehicles.
MirrorLink
MirrorLink is one of the most popular protocols which effectively mirrors a user’s smartphone to the infotainment system. It is done through a pair of applications on both the vehicle’s In-Vehicle-Infotainment and the smartphone. These applications might have a number of programming vulnerabilities which allow an attacker to manipulate the In-Vehicle-Infotainment system. This protocol does not have a secure device pairing.
As a result, this loophole enables hackers to gain access to not only the In-Vehicle-Infotainment systems but also CAN controller, which can affect critical safety systems such as manipulating navigation instructions.
Remote keyless entry
Previously only found in luxury cars, this feature has made its way into a greater number of vehicles. Passive Keyless Entry and Start (PKES) rely on bidirectional challenge-response schemes. A valid response unlocks and deactivates alarm systems, once activated the engine is then capable of starting. The passive and touchless nature of remote keyless entry provides the potential for replay attacks. Contrary to PKES is remote keyless entry (RKE), which relies on unidirectional data transmission (RF frequency oscillation) from the remote control embedded within the key.
These attacks are also susceptible to replay attacks. These are susceptible to weak cryptography keys and potential side-channel attacks.
STAY TUNED
Coming next month
In our next edition, we will explore various means for defending a vehicle against vulnerabilities and attacks by focusing on state-of-the-art cybersecurity defense mechanisms in CAVs.
Our partners:
Recent thought leadership
QAC EmTech QAC Emerging Technologies Quality Assurance This monthly newsletter will focus
QAC EmTech QAC Emerging Technologies Quality Assurance This monthly newsletter will focus
QAC EmTech QAC Emerging Technologies Quality Assurance This monthly newsletter will focus
QAC EmTech QAC Emerging Technologies Quality Assurance This monthly newsletter will focus
QAC EmTech QAC Emerging Technologies Quality Assurance This monthly newsletter will focus
QAC EmTech QAC Emerging Technologies Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus
QAC Automotive and Robotics (QAaR) Quality Assurance This monthly newsletter will focus